Training your employees to spot phishing emails is no longer a luxury. It’s an absolute necessity.
When the pandemic hit, we were hurtling towards a cyber, cloud-based marketplace. Since then, online work has become more popular
And so has cybercrime.
2020 featured some of the biggest hacks ever, and it’s likely only a sign of things to come. We learned that no victim is too large, as we saw with the Microsoft attack and the numerous breaches into the U.S. government.
And no victim is too small. Hackers are targeting small to mid-size businesses more than ever. And one of the most common ways they infiltrate businesses is not through software vulnerabilities. It’s through human vulnerabilities.
Why It’s So Important to Train Your Employees to Spot Phishing Attempts
Hackers are constantly on the hunt for weaknesses. Sometimes it’s a flaw in a security system. Sometimes it’s a missed software update. But the biggest vulnerability of them all is human error.
That’s how a teenager hacked into the Twitter accounts of celebrities like Elon Musk and Jeff Bezos. He used a spear-phishing technique targeting specific Twitter employees. Once he tricked them into giving up their information, he could hack into high-profile accounts to run a Bitcoin scam.
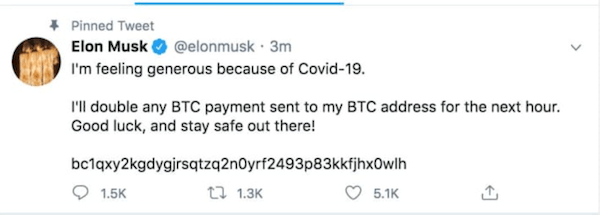
Three North Korean hackers were recently charged with stealing millions of dollars from banks worldwide. They also used spear-phishing techniques.
Phishing and social engineering are the most common techniques of hackers.
And they don’t just use these tactics against banks or huge corporations like Twitter. According to CNBC, small businesses are targeted by hackers 43% of the time, and yet they were only prepared to defend themselves 14% of the time.
That means that small businesses have become some of the easiest targets. They’re untrained, unprepared, and uneducated about the risks they’re taking.
According to the National Cyber Security Alliance, 60% of companies go out of business within six months after falling victim to a data breach.
If you want to protect your business, start with the most vulnerable and easily correctable aspect of your business—your employees.
5 Tips to Spots Phishing Emails From a Mile Away
1. Beware of Alarming Emails
Hackers don’t want you to think. They want you to act. And there’s no better way to achieve this outcome than to instill panic in a victim.
Phishing emails will often try to get you into your emotions by creating fear. They might appear to be from a legit platform that tells you that you’ve been hacked or that your account will be closed if you don’t act immediately.
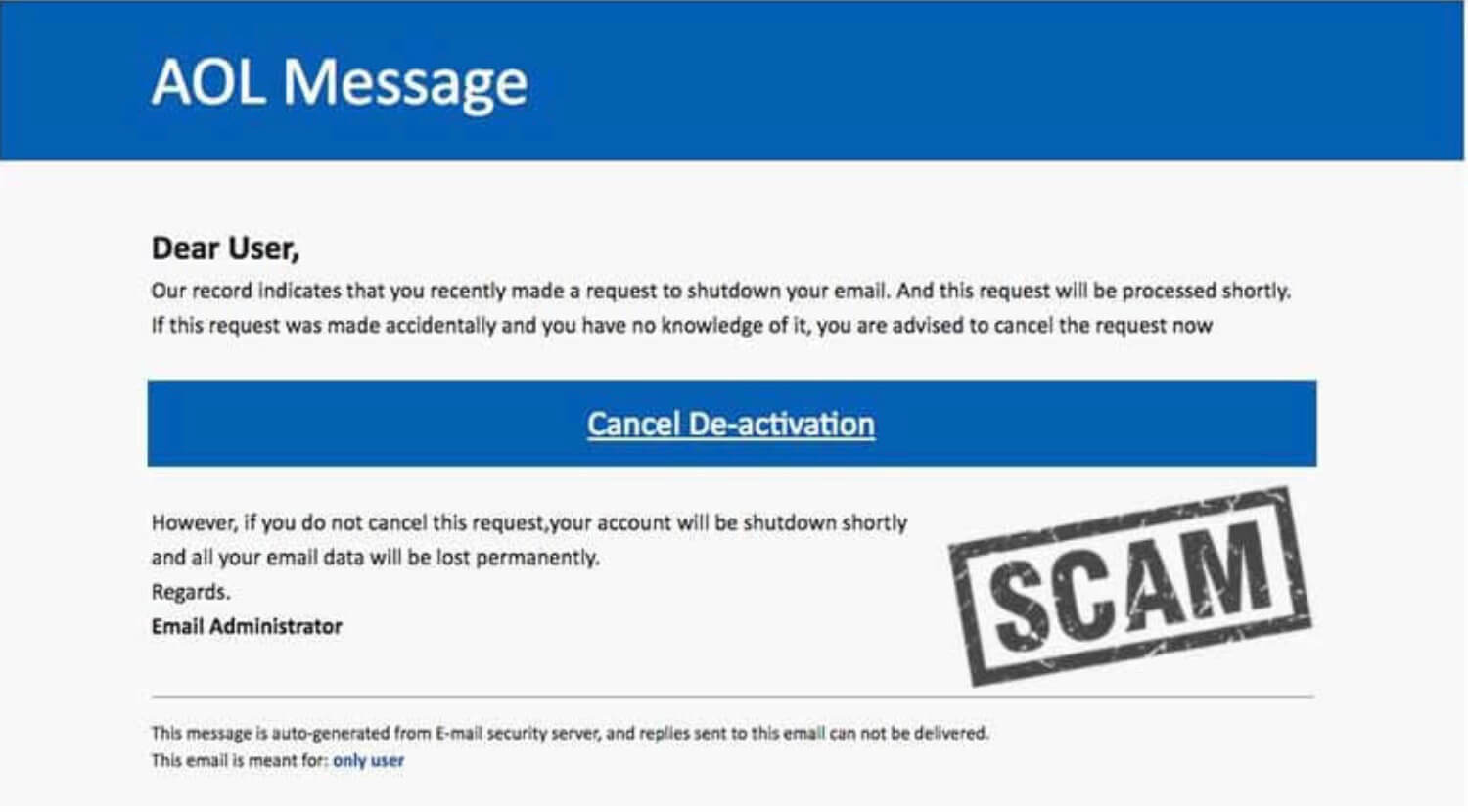
Any time you feel panic from such an email, take a breath and check for the other tell-tale signs of a phisher.
Conversely, sometimes these emails are ‘too good to be true.’ They might tell you that you’ve won money, and you only need to click on their (malicious) link.
2. Check For Suspicious Email & Web Addresses
While hackers can create imitation websites that look real, they can rarely create legit email addresses and URLs. Always look at who’s sending the email. It was the best way to spot the recent Instagram copyright infringement scam.
Hackers got people emotionally involved by telling them they infringed on a copyright and that their account would be deleted. They sent it through an email that looked Instagram-official.
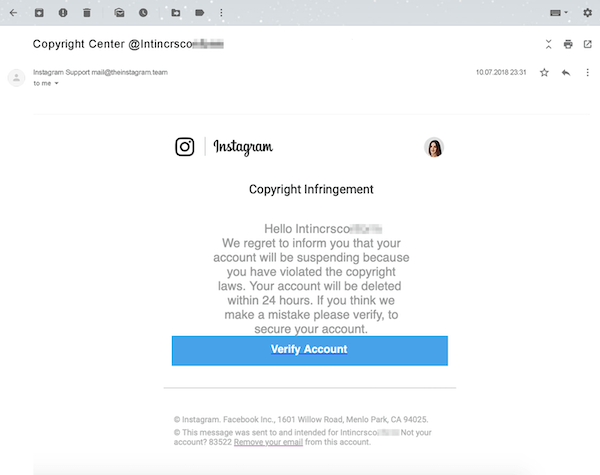 Looks legit, doesn’t it? | Source: Kaspersky
Looks legit, doesn’t it? | Source: Kaspersky
But upon closer examination, you can see it was sent from an email address ending in ‘theinstagram.team’ instead of ‘instagram.com.’
Always make sure the sender is legitimate by checking the email address. And hover over any links before clicking them to be sure they’re real.
3. Check for Bad Grammer
Phishing attempts often will be riddled with odd language or bad grammar. They might greet you with a word like ‘dear.’

If something feels off, that’s usually because it is.
4. Attachments = Red Flags
Real businesses in 2021 will rarely ask you to download an attachment. If they do, your spidey sense should be tingling.
But hackers love attachments. That’s how they can insert malware or ransomware into your computer. Always be suspicious of email attachments, especially ones with extensions commonly associated with malware (.zip, .exe, .scr, etc.).
5. Be On the Lookout for Sensitive Data Requests
Be extremely cautious any time a message requests sensitive data from you. Any request for login information, payment information, or personal details should be heavily scrutinized.
If you think the email is legit, don’t use any of the communication options provided. Rather, email the company directly with your concerns.
Conclusion
While these tips are helpful, they’re only the tip of the iceberg. If you want to prepare your employees, invest in training and a security culture.
Featured image by wk1003mike via Shutterstock.com