Hacking techniques are growing more sophisticated. Hackers are constantly coming up with new ways to breach accounts and steal data. After we dubbed 2020 “The Year of The Digital Pandemic,” techniques of 2021 are more frightening than ever. Below are some methods hackers use to get their hands on your private data and social media accounts.
Social Engineering – The Most Used Hacking Technique

By far, the most-used and least-understood hacking technique is social engineering. Hackers use numerous variations of this technique to get victims to give up their own information rather than directly stealing it. This is also by far the hardest hacking technique to protect yourself from, as any digital account can be breached by it.
Phishing is one of the most common types. Hackers will send e-mails or other messages posing as someone in a position of trust. They’ll then attempt to lead the victim into handing over their own information. Commonly, these messengers claim to be contacting you from a bank or company you’re familiar with, aiming to get your login or account details.
Facebook Warning: If you receive a message from one of your Facebook friends telling you that they are sending you a code to your phone to verify their own account, do not send the code to your friend! That could be a hacker that has taken over your friend’s Facebook account and now he/she is trying to social engineer you.
Another form of social engineering is digital blackmail. Some hackers will send messages claiming to have some sort of information that you wouldn’t like to be leaked to the public. This can range from proof of using pornography to having naked or otherwise compromising photographs of you.
Because social engineering is so popular, many different forms have been developed. Quid Pro Quo engineering has hackers posing as technical support to get victims to compromise their own systems. Baiting is another method where hackers will leave infected USB drives in public. Curious victims place these drives into their machines, and they automatically install keyloggers or other hacking software.
If you’re worried about social engineering, check out our guide on identifying scam emails.
Viruses, Worms, And Other Malware – The Most Well-Known Hacks
The type of hacking most people tend to think about when they hear the word involves viruses, worms, or other malware. Malware is an umbrella term used to identify the software installed on someone’s system with malicious intent. There are various types of malware because this type of software has been in development for as long as computers have existed.
Worms are a self-replicating type of malware hackers will install onto your system’s memory. Once installed, this software can slowly infect your entire system or potentially your entire network. This type of malware can change system files, steal your data directly, or even open a backdoor for hackers to control your entire system.
A virus is another type of malware that relies on the victim activating the infected file themselves. Viruses are often downloaded from shady websites, usually by people who don’t know any better. Once installed, they have similar capabilities to worms, such as stealing information or installing backdoors.
Trojan horses are a type of malware that masks itself as a different program. If you download software from an unreputable source or try to pirate software, it will often come packaged with a trojan horse. Once you’ve installed your program, it will often work as expected, but in the background, the trojan horse will collect your data or control your PC while you’re unaware.
Ransomware is one of the most obvious and dangerous types of malware. It gets onto the system through a virus, worm, or trojan horse, and then it completely locks up the system. Hackers force the victim to pay a ransom, often in bitcoin, to unlock their system. In some extreme cases, victims have paid millions of dollars to regain access to their network again.
Brute Force – A Mostly “Movie” Hacking Technique
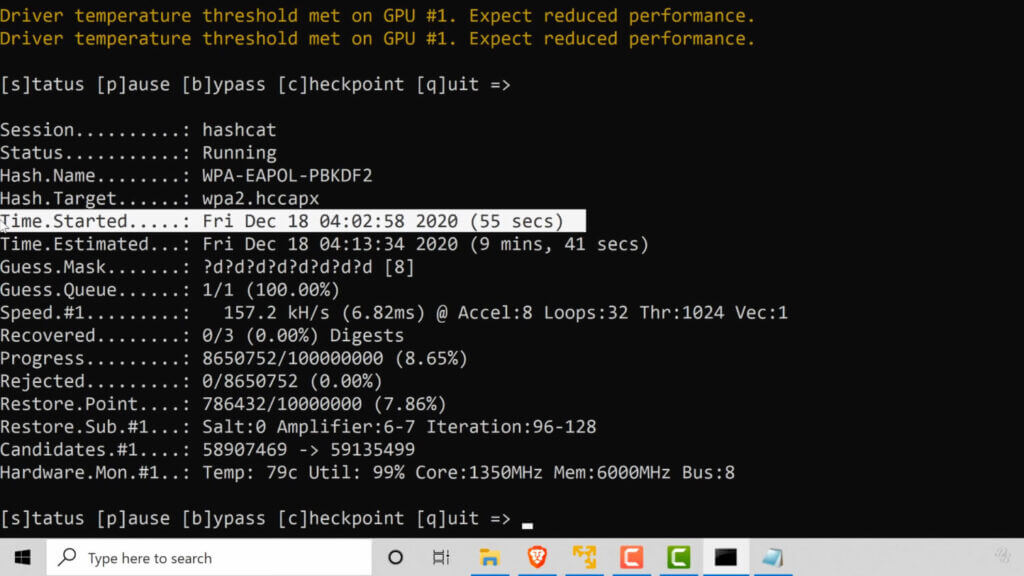
Brute force hacking is a method of hackers gaining access to a system by guessing the password. Specifically, brute force hacking requires the hacker to use software that guesses thousands of passwords at a time until the right combination of characters is selected.
In most cases, you only tend to find brute force hacks on the big screen. Running software to brute force a password doesn’t tend to work in real life. Almost every account online has a limit to how many times you can guess at a password before you’re locked out. Due to these limits imposed by system admins, brute force methods rarely have any chance of working at all.
The one exception to the rule is when it comes to WiFi passwords. It’s still possible to use brute force software on most WiFi routers because they don’t typically limit the number of password attempts you can make. It’s still possible for someone to gain access to your router and then to any computers connected to it. With some routers, it’s possible to add a limit to password attempts, but mostly this has to be done through complicated system commands.
Part of the reason WiFi routers come with unlimited password attempts is that a brute force program would take a while to work, and the hacker would need to be physically close to the router to even attempt the hack in the first place, making these types of attack rare.
Physical Breaches – Rare But On The Rise
Physical breaches are an extremely rare type of hack because they require someone to gain physical access to a system. In most cases, these sorts of hacks wouldn’t be possible. Companies tend to have a large staff and decent security procedures to prevent strangers from entering their offices and tinkering with their computers.
The recent pandemic has made these sorts of attacks much more viable. With reduced staff in offices, hackers have a much easier time walking in, going unnoticed, and hacking into systems with physically introduced software. While this hasn’t happened at a major social media company yet, there’s still a chance it might happen.
Security company Mitnick Security even suggested that 2021 could see an increase in these types of attacks, with many teams failing to update security despite much less foot traffic in their offices. The scariest part of this hacking method is that it relies on companies being on the ball. As an end-user, there’s not you can do personally to prevent these types of attacks.
Finally, Data Breaches
If you are unlucky, an online platform where you have a user might be breached. Hackers can steal the online platform’s database containing millions of user login data and private information like emails, passwords (often hashed), names, addresses, and phone numbers. If this happens to a platform where you have a user, you tend to receive a security email from the platform asking you to change your password immediately. Remember to change that password on every online account that might be using it!
If you’re worried about your personal security, get a comprehensive security audit here.
Featured image by Roman Samborskyi from Shutterstock.com