Google is one of the world’s biggest internet companies. They provide search engine services for billions of people and have their hands in online video streaming, game streaming, and just about anything else you can think of. A Google account is pretty much a necessity in modern life. But that doesn’t mean that your Google account is safe from hackers.
Watch our Google Recovery Video Below
So what should you do if you lose access to your precious Google account? Here are the steps you need to take if your account gets hacked.
1. Act Immediately
As with all online account security, quick action is essential. The longer someone has access to your account, the more damage they can do to it. The second that you detect some suspicious activity in your account, you should take steps to secure your account.
2. Change Your Password
If you can still get into your Google account, your first step should be to change your password.
Go to your google account page by clicking on your face in the top right corner.
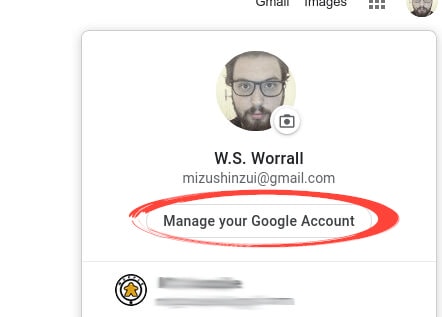
Click ‘Manage Google Account.’
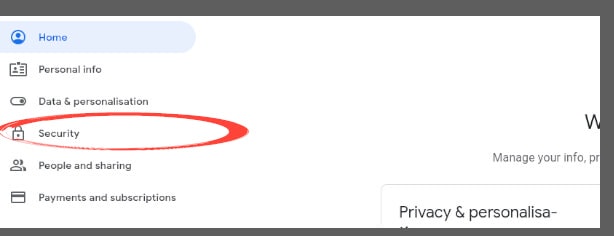
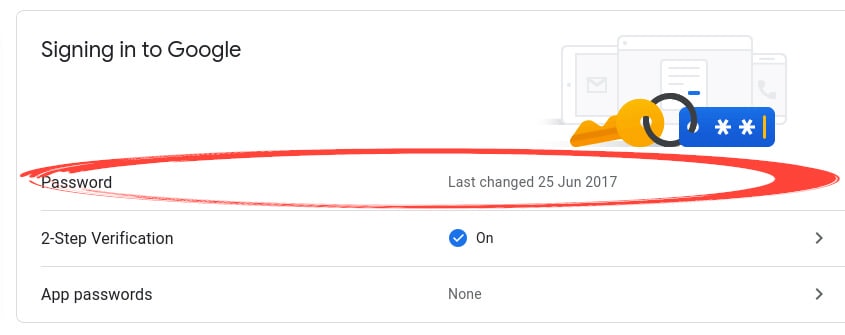
Click ‘Security’ on the left side of the page.
Click on the ‘Password’ section.
 Enter your new password twice to confirm and click ‘CHANGE PASSWORD.’
Enter your new password twice to confirm and click ‘CHANGE PASSWORD.’
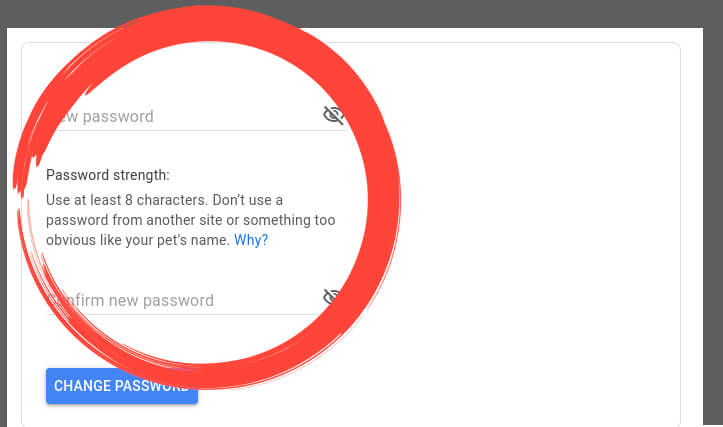
If you’re worried about having a strong password, visit our guide on common password mistakes.
3. Google Account Recovery
If you can no longer access your Google account, you’ll need to attempt to recover it.
Go to the Google login page and enter the email address of your account. On the password screen, click ‘Forgot password?’.
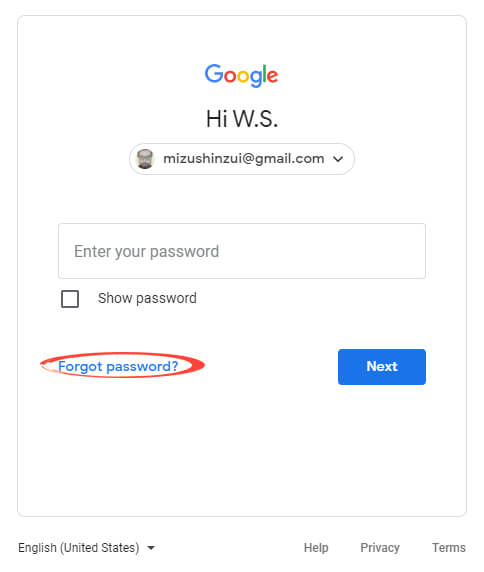
Enter the most recent password that you can remember for the account.
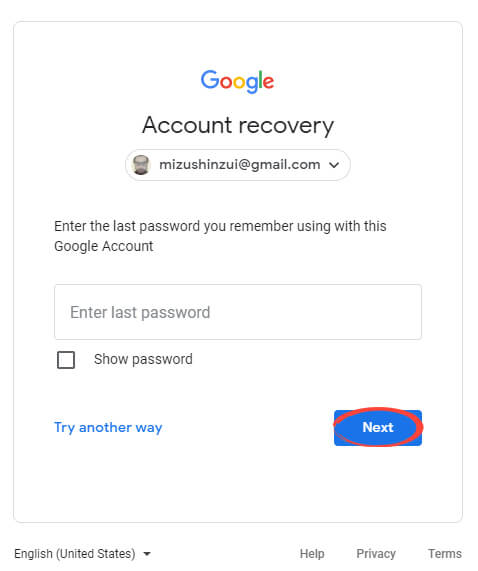
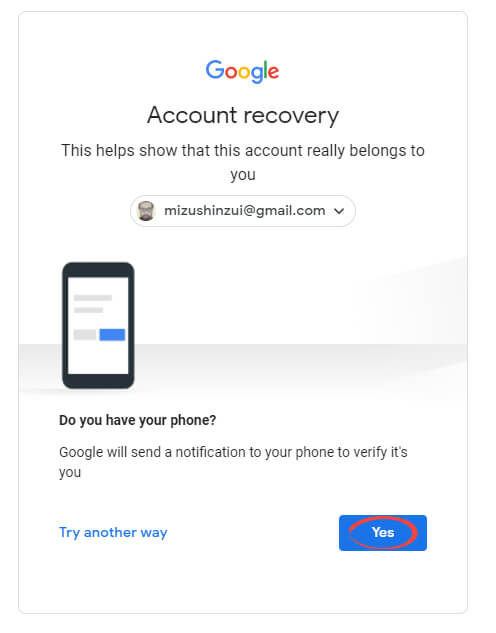
If you have access to the correct phone, click ‘Yes.’ If not, click ‘Try another way.’
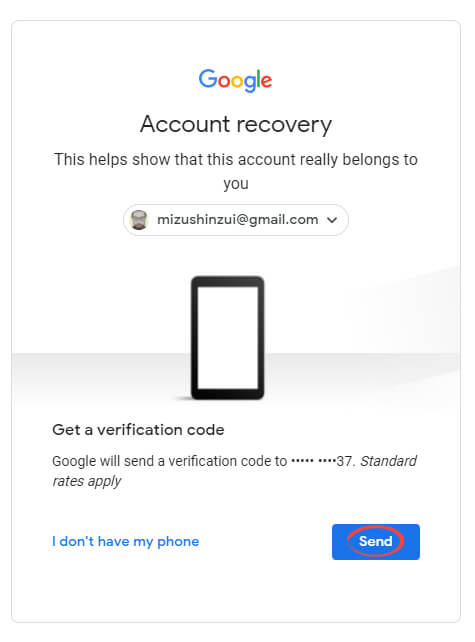
If you have access to the correct phone number, click ‘Send.’ If not, click ‘I don’t have my phone.’
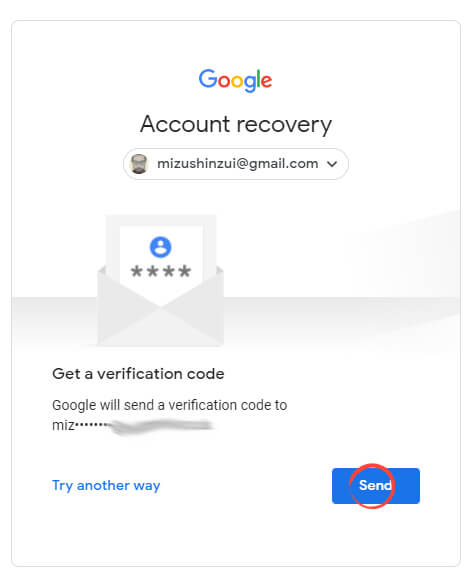
If you have access to the correct email address, click ‘Send.’ If not, click ‘Try another way.’
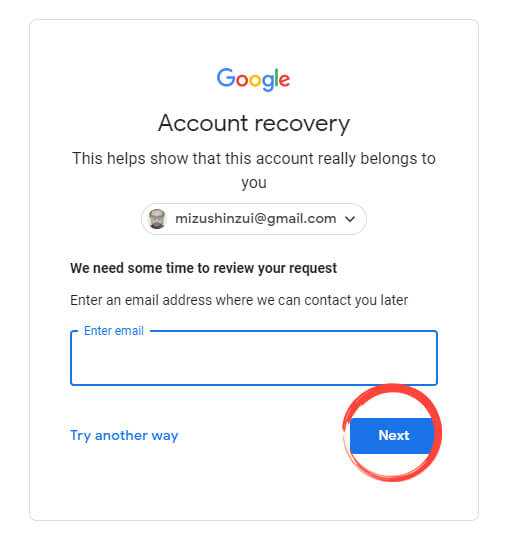
Enter an email for Google to contact you and hit ‘Next’ to have them contact you about your account recovery.
Once you’ve regained access to your account, visit our guide on securing your Google account.
Google image by TY Lim from Shutterstock.com