Everything from social media accounts to email addresses can be attacked anytime. Old accounts can put your new accounts at risk, so how can you tell if your accounts or passwords have been hacked?
7 Telltale Signs You’ve Been Hacked
In the age of digital connectivity, ensuring the security of our personal and professional data has never been more critical. Cybercriminals are always looking for ways to infiltrate and exploit your digital world. Recognizing the warning signs that your online accounts or devices may have been compromised. This article will dive into seven telltale signs that you’ve been hacked and provide practical advice to protect yourself from future cyber-attacks. Stay informed and stay secure!
Unusual Account Activity
If you notice any unexpected activity in your online accounts – like unsolicited emails, social media posts, or password change requests – it could be a sign that your account has been hacked. Keep an eye on your sent messages and account notifications, and always use two-factor authentication (2FA) to add an extra layer of security.
Device Performance Issues
A sudden drop in your device’s performance may indicate that a hacker has injected malware or is utilizing your resources for nefarious purposes. Watch out for unexplained slowdowns, crashes, or excessive data usage. Install reliable antivirus and malware protection software to identify and remove malicious files.
Unexpected Software Installations
Finding new programs or apps on your device that you didn’t install could be a sign of a breach. Cybercriminals may use your system to spread malware, launch attacks, or gain remote access to your data. Always verify the source of new software and keep your operating system up-to-date with the latest security patches.
Altered Browser Settings
You may have been hacked if your browser’s homepage or default search engine has been changed without your consent. Cybercriminals can manipulate browser settings to redirect you to malicious websites or display intrusive ads. Check your browser’s settings, remove suspicious browser extensions, and run a malware scan to identify and remove any threats.
Unauthorized Financial Transactions
Monitor your bank statements and credit card activity closely for any signs of fraudulent transactions. Hackers can use your financial information to make unauthorized purchases or steal your identity. If you spot any suspicious activity, notify your financial institution immediately to freeze your accounts and investigate the issue.
Mysterious Files or Folders
Finding unknown files or folders on your device can signify a cyber intrusion. Hackers may plant malicious files to access sensitive data or use your device as part of a larger attack. Use a trusted antivirus program to scan your system and remove any threats.
Ransomware Attacks
If your device displays a message demanding payment in exchange for unlocking your files or data, you’ve likely been targeted by a ransomware attack. These attacks encrypt your files and demand payment, often in cryptocurrency, to restore access. Do not pay the ransom, as it encourages further attacks, and there’s no guarantee your files will be recovered. Instead, contact a cybersecurity professional for assistance.
Use ‘Have I Been Pwned?’ to check if your private data has been leaked online
‘Have I Been Pwned?’ is one of the best tools for checking your email accounts’ safety. You should go to the website and enter each of your email addresses. The site will check if your account has ever been part of a data breach or if your account details have been pasted to the public online. If either is true, you know the account is more at risk.
You should secure any accounts that are at risk. Use a password generator and manager, and be sure not to open suspicious emails. It would help to be vigilant for suspicious activity on your email account. If you use the same password as the email account anywhere else, change it immediately.
Use ‘Dehashed’, a more advanced service
Dehashed is another powerful tool for checking the safety of your online information. Unlike the above tool, Dehashed covers more than email addresses. You can enter any search term, such as an old username, and the site will trawl the internet to see if any of your information is publicly available. The site includes tools to help you remove any personal data entries.
You should use Dehashed if you’re worried about old usernames you no longer use becoming compromised. Searching for your full legal name, address, and phone number is possible. For security reasons, you’ll need to create an account before you can check the details of any data you come across.
Check if sites you are visiting often are safe
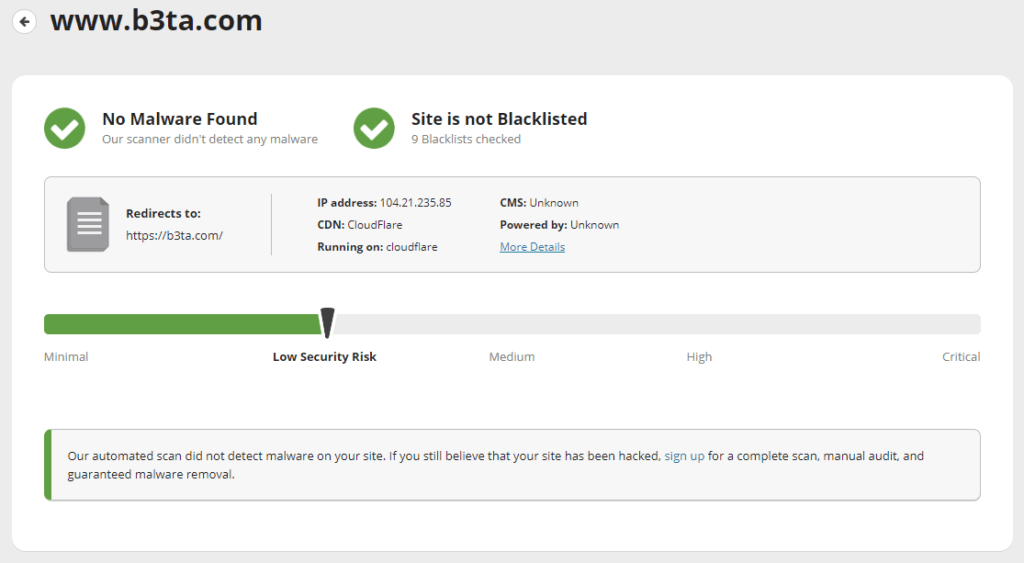
You should check sites you regularly use to ensure they’re safe. You can use free services, like Sucuri Site Checker, to ensure the sites you visit often are safe.
Go to Sucuri Site Checker and enter the address of any website. The site will provide you with a list of potential risks from the site you entered. If any sites you use regularly come back as risky, you should act immediately. It would be best to change any passwords associated with the breached site.
Monitor a List of Hacked Websites and Platforms
‘Have I Been Pwned’ offers a comprehensive list of all the websites that have ever been breached. Other sites, such as Self Key, list the most recent breaches. You can check these lists frequently to ensure that the sites or platforms you use haven’t been the victim of a data breach.
Most sites inform their users when a breach occurs. However, it’s possible to miss those messages; sometimes, websites fail to notify users promptly. You should check these sites regularly for your safety and peace of mind. If you want to keep updated, use an RSS reader like Newsflow and add the ‘Have I Been Pwned’ breached sites RSS feed. The feed will inform you whenever a new breach happens.
If you know you’ve been hacked, learn what you can do here.
Featured image by Suttipun from Shutterstock.com