In some ways, we’re just like hackers. We both want wealth, and we’d both prefer it to come to us easily.
The main difference is that most of us work hard for our money, while hackers steal it from us.
If this is a situation you’d like to avoid, it’s time to reevaluate your cybersecurity standards. By taking a few simple steps, you can exponentially increase your protection against cyber criminals.
Who’s Being Targeted?
While they may seem like mysterious cyber geniuses, hackers are also lazy.
Sure, they could probably find a way to hack almost anyone if they focused all of their resources on it, but more often than not, they’d rather hack someone unprepared and uneducated. And there’s no shortage of these targets.
According to a University of Maryland study, a hacking incident occurs every 39 seconds. Hackers affect roughly one in three Americans every year.
One reporter detailed her story of how a poorly secured GrubHub account may have led to hackers stealing $13,000 from her bank account.
Check out this video about how hackers accessed hundreds of bank accounts:
Even business owners have failed to meet the growing needs of the rapidly shifting cybersecurity landscape. The statistics are disturbing.
According to Fundera, hacking incidents against small businesses increased 424% in 2020. And yet, a BullGuard study showed that 60% of small business owners think they’re unlikely to be attacked. One-third of these businesses reported using free, consumer-grade cybersecurity software to protect their businesses.
In short, hackers have plenty of options when searching for easy targets. Here’s how you avoid being an easy target while protecting your hard-earned wealth from hackers.
5 Steps to Protect Your Wealth From Hackers
1. Enable multi-factor authentication
This should be step one whenever you open a sensitive financial account. Whether it’s your bank account, Postmates account, or Coinbase account, always set up two-factor authentication (2FA) on any account containing your sensitive information.
For some, 2FA may feel daunting, like some technically advanced step that only the savviest young tech minds can set up.
It’s not.
There’s usually an option within your account to enable this feature with the click of a button. And If you want to protect your wealth, this is a no-brainer.
2FA is nothing more than a 6-digit code that’s sent to your phone every time you log in. It can be texted or given to you by an app like Google Authenticator that gives you the code whenever you open it.
In short, it’s a second layer of protection against hackers. And for them to access your code, they would need physical access to your device. That is much harder to come by than digital access to your accounts.
According to one study, nearly 70% of black hat hackers said that multi-factor authentication and encryption were their biggest obstacles.
2. Get password savvy
Passwords are your first line of defense. And for many people, they offer very little resistance.
It’s not the passwords’ fault; it’s just that users often fail to heed these basic principles when creating a password:
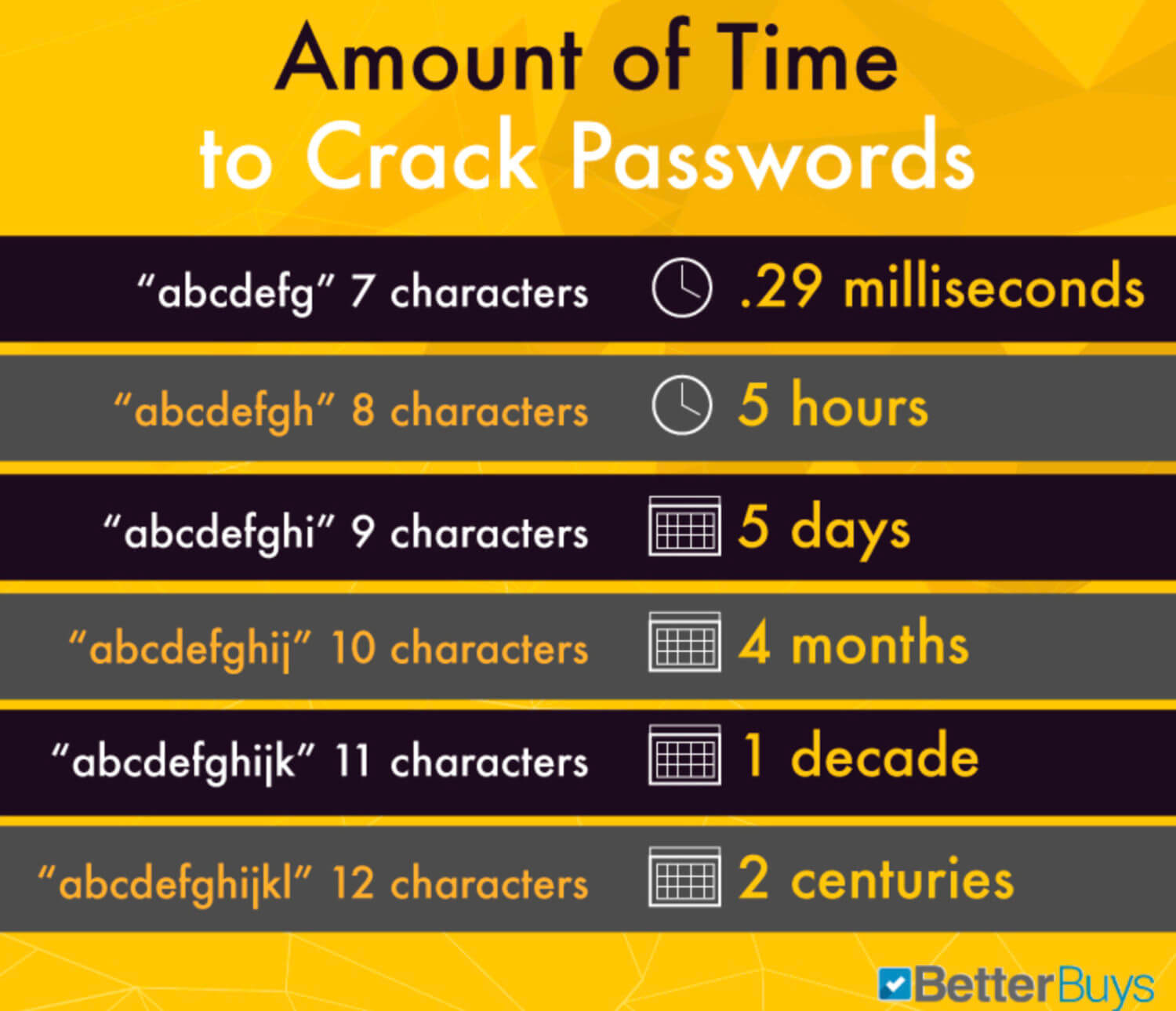
- Create long, varied passwords. Passwords become exponentially harder to crack the longer they get.
- Don’t use personal information. Hackers can find your information online in places like social media accounts and use it to try to crack your password.
- Don’t use predictable patterns. Stay away from predictable patterns such as ABC or 123.
- Use different passwords. It may be easier to remember the same password, but that also means that hackers will have access to multiple accounts if they manage to crack one.
- Use a password manager. If it sounds daunting to remember many different long, varied passwords, invest in a password manager like LastPass or Keeper.
3. Learn to spot phishing attempts
Phishing and social engineering are the most common techniques of hackers. While some cybercriminals are ready to pounce on the first software vulnerability they can find, many find that the human mind is the most vulnerable computing system of them all.
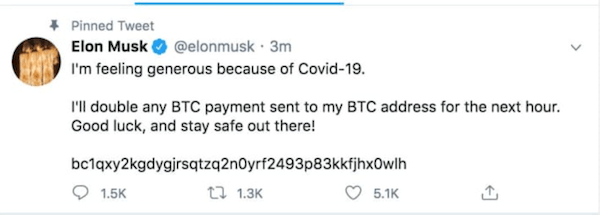
It’s often easier to just trick someone into handing over their sensitive information than to find and exploit a software flaw. That’s how celebrities like Elon Musk and Barack Obama were caught in a bitcoin scam on Twitter.
Luckily, phishers have some major hurdles to overcome if they want to trick someone who’s been trained in their ways. Here are a few tips for catching a hacker in disguise:
- Beware of threatening emails. Hackers want to act from your emotions, so they often up the urgency in their emails. Sometimes they’ll tell you that your account has been hacked or that it will be shut down if you don’t act immediately. Take a breath before you click anything and check for inconsistencies.
- Check for suspicious email addresses. Hackers can mimic a company’s email layout quite accurately, but they usually can’t send it from a legit email address. In the Instagram copyright infringement scam, they used the email ‘theinstagram.team’ instead of ‘instagram.com.’
- Check for bad grammar. Many times, phishing attempts will be riddled with odd language or bad grammar. They might greet you with a word like ‘dear.’ If something feels off, it’s probably because it is.
- Attachments are red flags. Businesses rarely need to send attachments to customers these days. More often than not, it’s a cybercriminal trying to get you to download malware.
Thieves can also create fake banking apps and post them on the App Store. Make sure you check out the number of reviews an app has before downloading it. If it’s posing as an ‘official’ banking app and has very few reviews and comments, it’s likely, not legit.
4. Invest in encryption software
Encryption software has become widely accessible and fairly affordable these days. This software encrypts the data and activity on your computer, making it far more difficult for hackers to access your information.
There are several different types of encryption software. Some encrypt specific files, some encrypt your entire device, and some services, such as a VPN, encrypt your online activity.
Check out this video explaining VPNs:
5. Don’t use public wifi
If you frequent public places such as libraries or coffee shops, where a password does not protect the internet, you expose yourself to risk. Hackers can use unprotected wifi to gain easier access to your personal information.
Even if your banking password isn’t saved on your computer, they can still access details from your life that may help them infiltrate some of your accounts.
Get a Free Risk Assessment from Hacked.com
We are now offering a free risk assessment with our Personal Digital Security Manager plan that you can learn more about here.
If you have any questions about your cybersecurity needs, contact us at help@hacked.com or book a free consultation call today.
Featured image by Elnur from Shutterstock.com