The threat of blackmail and extortion has become more common. Cybercriminals use various techniques to obtain blackmail material, while scammers may deceive their targets into thinking they hold such information, with the intention of demanding money. Coping with such situations can be challenging, but this article aims to provide you with some helpful tips on how to effectively combat these issues online.
Learn how to handle and stop blackmail here. Sign up for free lessons.
Different types of online blackmail
There is a distinction between blackmail and extortion.
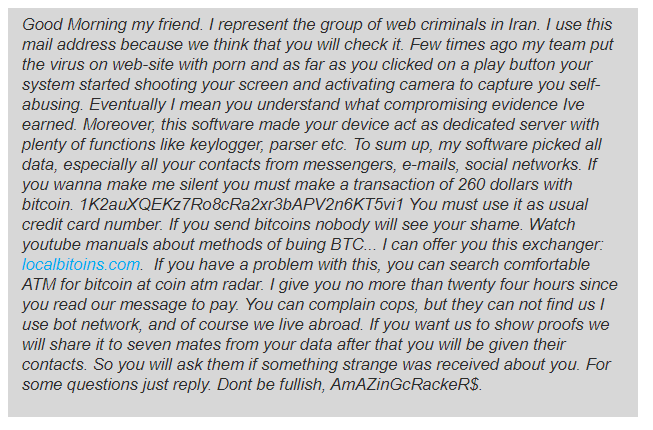
When someone threatens to reveal embarrassing information about you, that is blackmail. An excellent example of blackmail is the “blackmail for watching porn” case. These scammers threaten to release videos of the victim watching pornography to their family and friends unless they pay.
Extortion, on the other hand, involves some form of threat of harm. In the real world, extortion usually involves threats of violence, but not in the digital world. Online, an excellent example of digital extortion is ransomware. Malicious software designed to lock a victim’s computer unless they pay a ransom is a clear example of digital extortion. Or the claim of having nude images or sexually related videos of yourself or someone you know, and the threat to publicize this material. Which is also called sextortion.
These are serious criminal offenses in both cases, and you should treat them accordingly.
How to Fight Blackmail and Extortion
Dealing with online blackmail and digital extortion can be incredibly stressful and overwhelming. It’s important to remember that there are different approaches to take depending on the specific situation. You can learn what to do if you are blackmailed here.
Online Blackmail
Depending on the type of online blackmail, there are a few things you need to do. The first step is for you to determine whether the blackmailer is a scammer or a hacker. Our guide on the pornography blackmail scheme will teach you how to spot a scam.
The key point is to look out for proof. When a simple blackmailer messages, they’ll often provide you with evidence of the material they have on you. If someone sends you a message that doesn’t refer to you by name and contains no images, footage, or other harmful content, it’s almost certainly a scam.
If you’re convinced that your blackmailer is a scammer, you can safely ignore them without concern. If you are uncertain, schedule a video call with us here.
You should carefully consider your response if the hacker proves themselves legitimate. Under no circumstances should you pay the hacker. If you pay, the hacker will keep demanding more money in the future, creating a never-ending cycle.
In most cases, your best option is to face the subject of blackmail itself. If it’s something you can come to terms with, sharing it yourself removes all power from the blackmailer. The blackmailer won’t make money from you without anything to embarrass or harm you with. However, this should be a last resort.
Digital Extortion or Sextortion
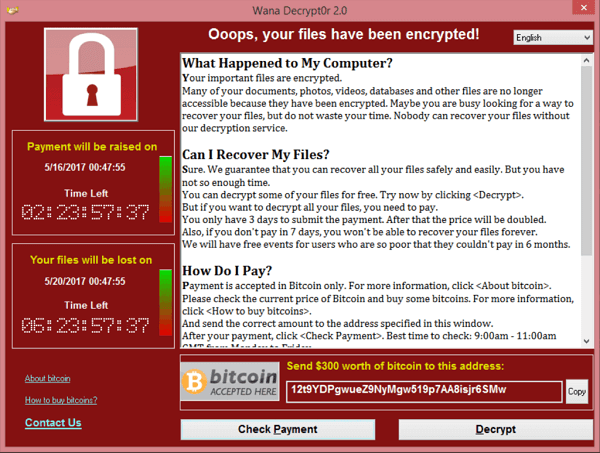
Digital extortion can be a little harder to deal with than online blackmail. If your computer or other devices are being held for ransom, you should immediately stop using them. Disconnect affected devices from the internet and make sure they remain switched off. If you continue using blocked devices, you could cause further harm.
Avoid paying the ransom, as it’s doubtful that you will regain access to your devices afterward. Instead, hackers will likely retain access to your system, mine your data, or demand even more money.
If you’re physically threatened, then you should contact the authorities.
How We Can Help
If you’ve been the victim of online blackmail or digital extortion, get help here.
Featured image by arda savasciogullari from Shutterstock.com