Hackers have a wealth of tools to cause damage to your small business. From DDOS attacks to cryptojacking, it’s important to understand the ways hackers can attack you. This guide will teach you the most important aspects of how hackers can hurt your business.
Why It’s Important to Understand How Hackers Can Hurt Your Business
You should be aware of the different kinds of cyberattacks so you can easily recognize them. One of the most crucial parts of reducing damage from a cyberattack is recognizing what’s happening and responding appropriately and quickly.
When hackers attack your system, you must know which actions to take. The type of damage from these attacks varies wildly and, in some cases, can be incredibly subtle. Educating yourself is the best tool you have in your arsenal.
How Hackers Can Hurt Your Business
Hackers have existed as long as the internet, and their tools have grown incredibly sophisticated and numerous. Below is a list of the various types of attacks, signs to recognize them, and how you should respond.
DoS or DDoS
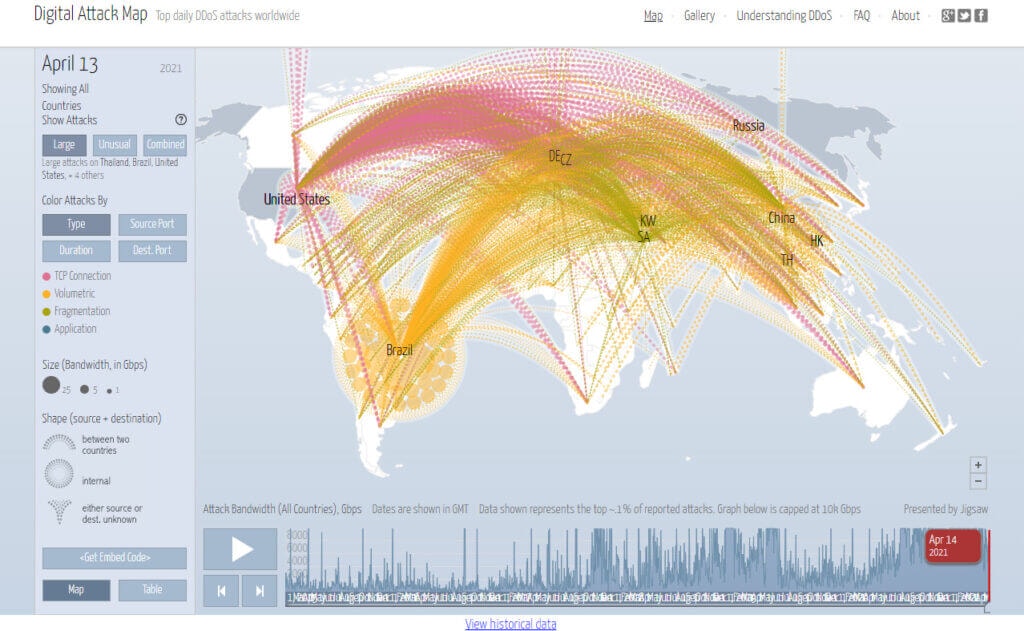
DoS and DDoS stand for denial-of-service and distributed denial-of-service, respectively. Hackers who use these attacks aim to make the target’s systems inaccessible through various means. In the most common form of the attack, hackers flood a system with many requests, preventing anyone from using it. The key difference between a DoS and DDoS attack is that it comes from multiple sources at once, making it much harder to stop.
Small business owners rarely need to worry about DoS or DDoS attacks. Hackers using these tools usually aim to take a site or service down rather than steal data or money. In most cases, hacktivists are responsible for these attacks, and they have a political or social agenda behind them, but other reasons for DoS attacks can include revenge or blackmail.
Unless your business is related to the government or goes against an extreme social ideology, you’ll unlikely suffer this attack. If you do suffer a DoS attack, the signs are pretty clear. When your website or server slows down or becomes completely inaccessible, it’s probably a DoS attack. Check your access logs and see if you’re flooded with external requests. If you are being flooded, temporarily shut down eternal access to your servers while you set up a form of request authentication. Cloudflare is one service that can help reduce DDoS attacks for websites and online services.
Cryptojacking
Cryptojacking is a style of attack that greatly impacts system performance. Hackers sneak software onto a target system designed to mine cryptocurrency in these attacks. Hackers often use backdoors or security exploits in a business’s software to sneak a mining program into their system.
These attacks can be so harmful that they prevent a business from accessing its full system power. The hacker’s mining software uses that power to mine cryptocurrencies from the internet. This means that systems begin to run slowly and reduce the company’s ability to do its job and make money.
The clearest sign of this type of attack is a sudden drop in your system’s performance. You can identify this type of attack by running a powerful anti-malware program across your entire system. You should check your business services if you identify this software in your system. When you find cryptojacking software, it means there’s a weakness in your security.
Malware Planting
Malware planting is the act of hackers breaking into a system and installing malicious software. This software is often implanted through a security vulnerability in the target system, but social engineering can also be used.
Hackers can install various types of malware, each with different purposes. Hackers use keyloggers for farming passwords or other key data. There is spyware, in general, which reports data to the hackers automatically. One of the most worrying kinds of malware is ransomware, which holds your system hostage, until you pay money to release it.
Regular security checks are the only real way to detect malware on your system. Ensure that you’re running scans of your system at least once a week and that your software is up-to-date. If you discover malware on your network, check your system. Malware is a clear sign of a breakdown in security, either through software vulnerabilities or human error.
Data Skimming
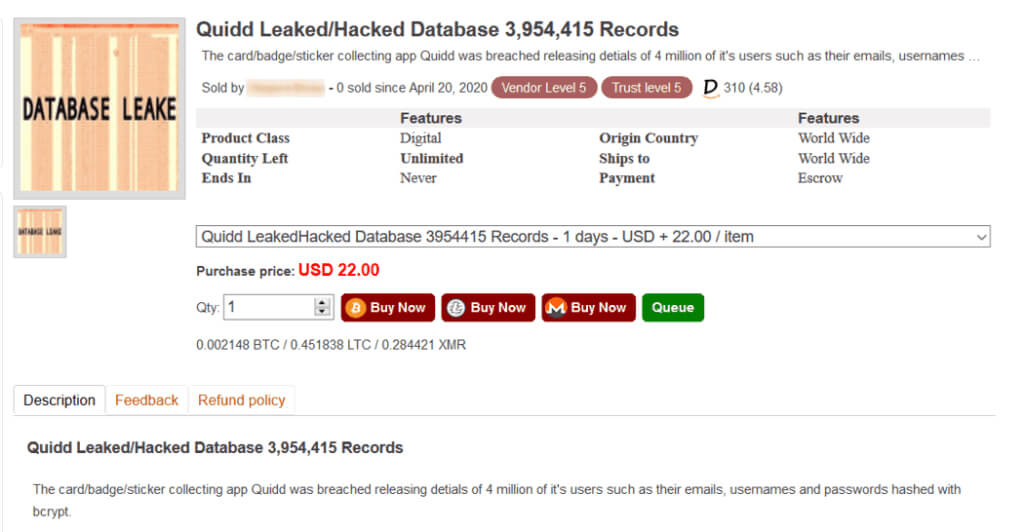
Data skimming is stealing data directly from a company’s system and is one of the most basic and common types of cyberattacks. Hackers will breach a system through social engineering or security exploits and attempt to set up a backdoor. Backdoors allow hackers to continue accessing a system without the owner’s knowledge.
Data skimming is a massive problem for a variety of different businesses. Exposed data can include banking information, clients’ data, or other sensitive information. Hackers will use this information to steal money from bank accounts or sell the data on the dark web. For more information on how criminals use the dark web to sell information, see our guide on the subject.
Detecting data skimming can be difficult, as there is no detectable damage to your system from data being stolen. The only real way to discover data skimming is to check access logs and ensure no unauthorized access occurs regularly. If you detect a backdoor or data skimming, close the security gaps and check your business services and cybersecurity practices for vulnerabilities.
Taking Over Social Media Accounts and Websites
If you use social media for your business, then this is another way that hackers can harm your business. Hackers can hack into your Facebook, Instagram, or other social media accounts related to your business. These hackers will typically hold these pages/accounts to ransom or sometimes even change their information to something completely different to make money on advertising. In either case, a compromised social media presence can hurt your brand and make you lose customers.
Your small business website can also be a target for takeover by hackers. A hacker can gain complete control over your website by cracking your hosting or content management platform. Not only does this prevent customers from learning about your services, but it can also be detrimental to your brand. In the past, hackers have changed banners, front page images, and text to reflect poorly on the company in question. And the hacker can steal your domain name if your domain manager is hacked.
Detecting a social media or website hack is simple. If you keep an active presence on your website or online accounts, you should be notified when account settings are changed, or a login attempt is made. As soon as you have any suspicion that you’re at risk, change your online passwords and ensure you have 2FA enabled. For more information about securing your online accounts, visit our guides on account security.
Socially Engineered Money Transfers
Socially engineered money transfers are dangerous to any business, online or offline. In this type of attack, hackers will usually pose as a bank, financial institution, the CFO of the company, or an online service/store and attempt to trick the victim into transferring money directly to them.
In some examples, victims have transferred more than $20,000 to scammers. The potential for harm is even greater if you’re dealing with business accounts.
The best way to detect this attack is to familiarize yourself with how these scams work. As hackers using this method rely on social engineering, education is your greatest asset. We have several guides on recognizing scams, including scam emails, scam texts, and even social media account scams. Familiarize yourself with how these sorts of scams work, and above all else, never transfer money without checking directly with the bank, person, or service in question first.
How We Can Help to Protect Your Business
If you’re worried about how hackers can hurt your business, we at hacked.com can help. Get in touch by emailing help@hacked.com or visiting our support page here.
Featured image by ra2 studio from Shutterstock.com