2020 has been one of the worst years for cybersecurity. Researchers have recorded a huge spike in phishing scams. Healthcare companies expect ransomware attacks to have quadrupled this past year. Despite data breaches increasing by 67% since 2014, only 33% of US citizens have ever checked if they’ve suffered a breach.
The Biggest Data Breaches and Hacks of 2020
The ongoing COVID-19 pandemic has seen a massive spike in internet usage from remote workers, including increased streaming and social media usage for private consumption. The FBI states that this spike in usage has increased cybercrime reports by as much as 400%.
In terms of data breaches, 2020 saw over 737 million files breached in total. The largest breach was from Estee Lauder, which had 440 million records targeted by hackers. Hackers also made off with an unknown number of email addresses.
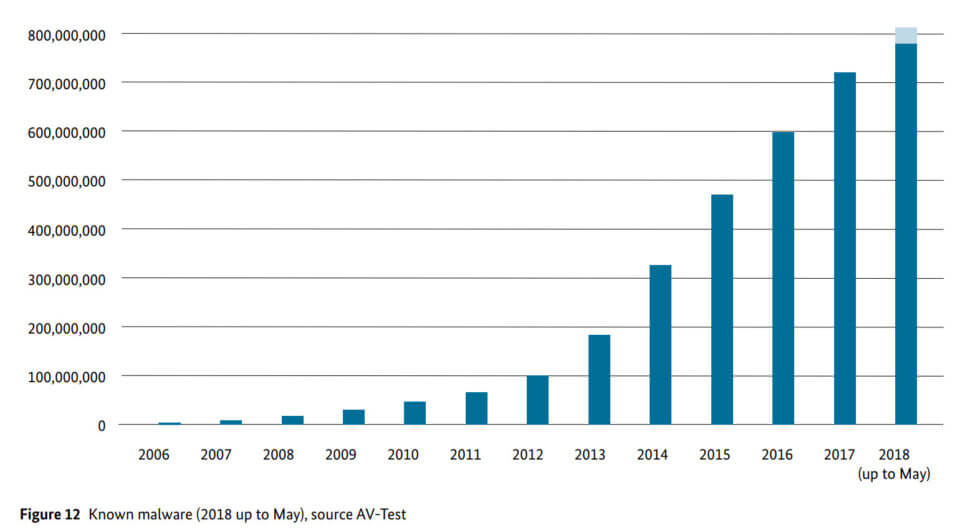
The breaches and hacks of 2020 show that cybercrime attacks have increased year-on-year. AV-test, a company that catalogs new forms of malware, has recorded a rapid increase in the new types of discovered malware. A stark increase in cryptojacking attacks, ransomware attacks, and phishing scams grew by 252%.
Below are some of the year’s biggest data breaches and hacked websites.
Wawa
In January of 2020, over 30 million payment cards appeared for sale on the underground black marketplace Joker’s Bazaar. Security Investigators traced the cards in this listing back to US convenience chain Wawa.
Wawa discovered the breach in December of 2019, but it is believed that the breach began 9 months in advance. Hackers got the information by installing malware onto Wawa’s payment software, potentially at a nation-wide level. Intelligence firm, Gemini Advisory, claims that even more payment cards could be at risk. Hackers released cards in batches to prevent the price of the information from dropping.
Estee Lauder
One of the biggest data breaches of the year was Estee Lauder in February of 2020. The cosmetic company had 440 million records accessed in a staggering breach of its security. Of the 440 targetted files, an unknown amount were plain-text email addresses.
Criminals uploaded an unprotected database to the internet, which contained over 440 million pieces of information. The database was discovered in late January by security researcher Jeremiah Fowler. It is unclear what method the hackers used to take the information or how long it had been available. Most of the files were middleware, software used by the company to manage everything from internal messaging to account authentication.
Hackers could use the information from the breach to create numerous back doors into Estee Lauder’s security, potentially compromising the website in the future.
Wishbone
Straw poll app Wishbone had 40 million user records leak in May of 2020. Hacking group ShinyHunters leaked the data on RaidForum, a popular database leaks marketplace.
The leaked database contained a lot of user’ information, including usernames, email addresses, mobile numbers, and even some password information. Password information was encrypted using the MD5 algorithm that has been considered unsafe for use for a decade. This outdated encryption makes it much easier for hackers to crack those hashes.
Hackers have targetted Wishbone in the past, leaking 2.2 million email addresses and passwords back in 2017.
Pakistani Mobile Users
Pakistani Mobile suffered a major breach spread across two separate incidents. Hackers put 55 million user accounts up for sale in April 2020. A month later, in May of 2020, hackers leaked another 44 million user accounts.
This major leak of data is still surrounded by mystery. The latest files discovered were entered into the database during 2013, prompting some to believe the breach took place up to 7 years ago. A security firm operating out of Isreal claimed that the breach might have occurred in 2017.
The information leaked included the users’ phone numbers, full names and addresses, and national ID numbers. No mobile company has come forward to accept responsibility for the breach, and an investigation by the Pakistan Telecommunications Authority is still ongoing.
T-Mobile Breaches
T-Mobile is a company with a poor reputation for cybersecurity, and 2020 saw another big hack of the mobile service provider. In March, the company began notifying users of a mysterious hack that exposed real names, addresses, phone numbers, and other sensitive information.
T-Mobile eventually revealed that hackers had gained access to an employee email address. It is unknown how many people may have been affected by the breach, as the company did not make any numbers public. After two breaches in six months, this is certainly bad news for T-Mobile customers.
CouchSurfing
Hackers obtained 17 million users’ information from the hospitality exchange service Couchsurfing. The information was theorized to have been stolen during a breach in early July 2020 before appearing on hacking channels and forums for sale.
As far as investigators can tell, no passwords were leaked during this breach. Hackers instead offered 17 million email addresses and real names for 700 USD. A dark web Data Broker claimed hackers might have extracted the data from an old backup file, which would explain the lack of any password information.
Nintendo NNID Hack
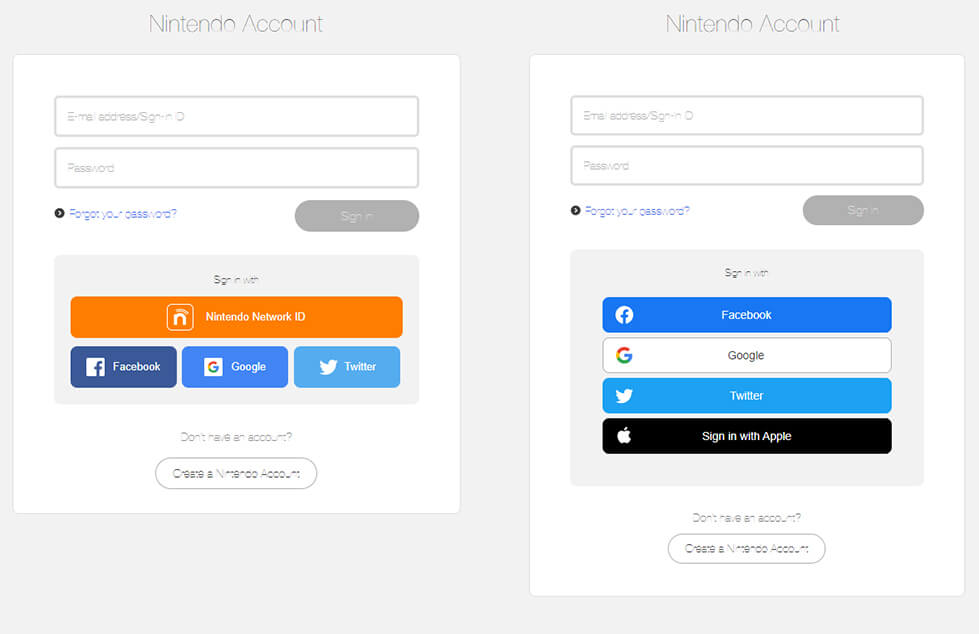
Japanese gaming Nintendo suffered a security breach in mid-May that exposed 300,000 accounts. Hackers then used various accounts’ payment information to make illegitimate purchases.
Nintendo’s legacy login method, NNID (Nintendo Network ID), was compromised, though it didn’t publically disclose many details. A Nintendo representative said that the attack appeared to have “spoofed login to Nintendo Network ID.” The company initially claimed that only 160,000 users had been affected, but those numbers were found to be closer to 300,000 by June.
Some users lost as much as 300 dollars to the hack, and users all over Twitter reported similar incidents.
MGM Resorts Breach
MGM Resorts suffered a breach in the summer of 2019. The company did not publicly disclose the breach until 2020 when hackers started selling the data on a cybercrime marketplace. The company did not reveal the severity of the breach, but 10.6 million users’ information was put up for sale in February. By July of 2020, the number of affected users skyrocketed by 14 times to 142 million users.
The data disclosed included full names and addresses, as well as dates of birth and phone numbers. Hackers claimed to have obtained the information by breaching Night Lion Security, a third-party that offers increased cyber-security to businesses. Vinny Troia, the company’s founder, claims the hackers are just trying to ruin his company’s reputation.
The head of research for cyber intelligence firm KELA speculates that the breach could be even bigger. According to posts on Russian-speaking hacking forums, up to 200 million users may have had their data stolen.
Experian South Africa
Experian South Africa suffered a social engineering breach that affected 24 million users. A hacker posing as a client gained access to millions of users’ information. This hacker reportedly intended to use the data to gain a marketing foothold in credit-related industries.
South African authorities recovered the data before the hacker could cause any harm. Experian claims that the hacker didn’t access any financial information.
European Medical Agency
Through the summer of 2020, Cozy Bear made repeated attacks on various medical companies involved in producing the COVID-19 vaccine. A currently unknown-group is responsible for a successful hack against the EMA. This hack exposed data relating to the COVID-19 vaccine devised by Pfizer.
Details on how the hack happened are scarce, but if there is a link between Cozy Bear and the EMA breach, it’s likely that custom Malware and Spear Fishing techniques were employed, as with their other attacks. These methods are highly targeted at specific individuals and companies, making them much more effective than more broad techniques run-of-the-mill hackers use.
FireEye
FireEye, a cybersecurity company that defends third-parties worldwide, announced on December 8th that they had suffered a data breach. Hackers accessed tools the company uses for penetration testing against its clients’ security. FireEye uses these tools to simulate a real attack by hackers.
According to FireEye, this attack was highly-targeted and sophisticated and likely came from a state-sponsored hacking group.
Experts have suggested that the Russian state-sponsored hacking group, Cozy Bear, is behind the attacks. Despite this, Moscow has denied any responsibility for the breach, blaming U.S. media for accusing them.
Google Going Down
On December 14th, Google experienced an outage that prevented users from accessing various services. The outage lasted for more than an hour and caused a storm of social media.
Cybersecurity expert Will Geddes claimed that the Alphabet Inc. outage could be part of the same cyberattack that affected the US government.
“…this is quite concerning, this could be the 9/11 of cyber hack attacks”
The potential hack against Google has affected nearly 70 million users across various services. Questions have been raised about the world’s dependence on certain online services and the potential damage to the economy.
SolarWinds Hack
SolarWinds is a company that provides IT solutions to various companies and government bodies around the world. In mid-December, the company revealed that a hacker had slipped an exploited update onto the service that left them able to access many files.
Hackers could access files from various big companies and US government departments for months. Cybersecurity experts have called this the biggest hacking attack of all time. Brian Lord, a UK-based cybersecurity expert, claims that the safest top secret files are safe, but we may never know exactly what was accessed.
Experts speculate that this attack is the same as the FireEye and Google incidents and that the Russian-backed group Cozy Bear is responsible. Currently, it’s not possible to confirm Russian involvement. Talking to the BBC., Professor Alan Woodward of the University of Surrey said, “the attack has the hallmarks of a Russian operation.”
The list of potential victims includes some high-profile names:
- The Office of the President of the United States
- The Secret Service
- The Department of Defense
- NASA
- Microsoft
- Mastercard
- Visa
- Lockheed Martin
- McDonald’s
- Comcast
The full list of clients is much longer but was removed from the SolarWinds website after the hack took place.
Who Are Hackers Targeting and Why?
Throughout 2020, hackers increased their activity by more than 600%. This increase in activity affects older people more than other age groups, as they’re more likely to fall for email phishing scams. People over 60 accounts for nearly a quarter of the money lost through cyberattacks each year.
Hackers have been responsible for over 4,000 attacks each day during 2020. There will have been over 1,460,000 attacks by the end of the year 2020. Nearly 90% of successful attacks occur thanks to human error, either by the target themselves or a third-party.
Cybercriminals used the fear of the ongoing COVID-19 pandemic to target home-workers with phishing scams. The percent of fraudulent mail targeting home workers jumped from 12% to 60% throughout the year.
Breaches Target Medical, Financial, and Small Businesses
Hackers frequently target small businesses, which make up 43% of the total breach victims. The most at-risk industries are financial and medical industries, storing a large amount of sensitive user data.
Cybercriminals target the medical industry to access patient files. Hackers can then use the sensitive information found in these breaches for further hacks and scams. Ransomware is one of the most common forms of attacks on the medical industry. The rate of ransomware attacks quadrupled in the past year. On average, hackers accessed 113,491 sensitive files during each breach of a medical company, one of the highest figures compared to other industries.
Financial services attacks are some of the most costly, with an average cost of $18.3 million per breach. 90% of attacks start with a highly targetted spear-phishing email that gives hackers access to a company’s servers. Hackers gained access to, on average, 352,771 files per financial services breach.
Tech Companies Struggling to Keep Up With Increased Attacks
Hackers’ increased activity is causing problems for social tech companies. The ongoing COVID-19 pandemic has caused sites like Facebook & Instagram to reduce staff. This understaffing means fewer people can get help to recover their accounts.
Microsoft has revealed in the past that 99.9 % of attacks could be prevented if multi-factor authentication is enabled on all accounts. If you need instructions on activating multi-factor authentication, also called 2FA or two-factor authentication, visit our guides about securing your online accounts.
To find out more details about the situation tech companies face during the pandemic, you can read our article about it here.
Featured image by Sasun Bughdaryan from Shutterstock.com