One of the biggest hacker attacks in history is still on-going and has been since 2006. Despite this, most people aren’t familiar with the name ‘Operation Shady RAT.’ Below you can find out the details of this attack that has been going on for over a decade, who is doing it, and why.
What is Operation Shady RAT?
Operation Shady RAT is the name given to an attack that has been developing since 2006. Dmitri Alperovitch, a security researcher, working for McAfee, originally reported and named the attack in 2011. Alperovitch discovered, over the course of 5 years, that the same group of hackers had targeted more than 70 companies and government entities around the world.
In his 2011 white paper, Aperovitch disclosed the hackers’ targets, how long they’d been attacked for, and what the hackers were stealing. In more than 10 countries worldwide, hackers were stealing valuable intellectual properties from companies and governments.
Although Aperovitch reported on these hackers in 2011, they were active from 2006 and onwards. To this day, many security researchers say that Operation Shady RAT is still ongoing.
Who Did The Hackers Target?
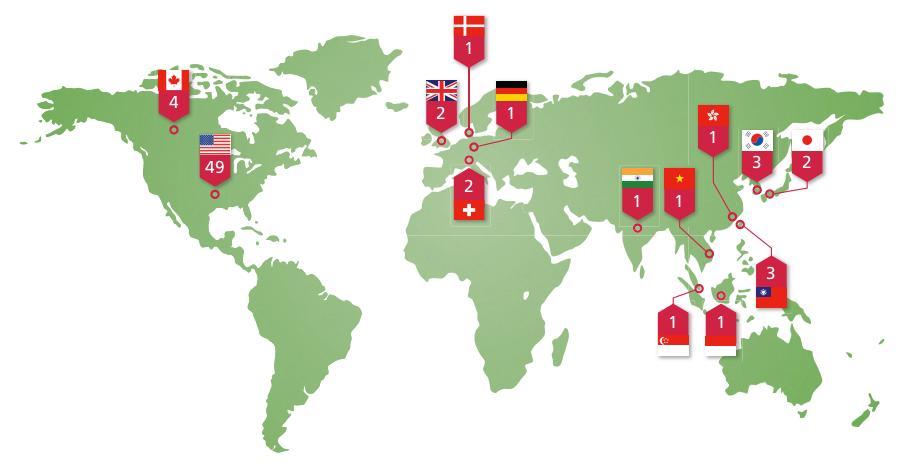
Shady RAT is one of the biggest cyberattacks in history, with over 70 targets. Despite many victims and the severity of the attack, researchers are still trying to confirm who some of the victims were.
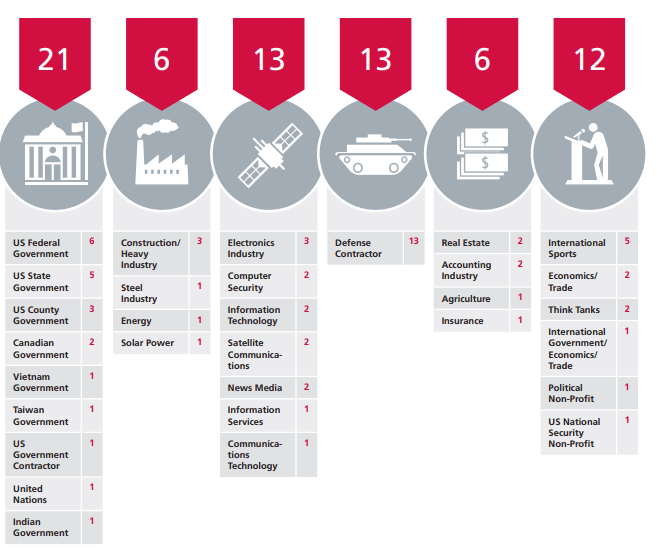
We know that some of the more worrying names on the list of targets include The U.S. Federal and State Governments, The Canadian Government, The United Nations, and defense contractors. In particular, hackers seem to have focused on targeting defense contractors, as they make up the biggest single group of victims in the report.
A lot of private companies also found themselves targetted by the hack.
What Did the Hackers Take?
The hackers behind Shady RAT were mostly after intellectual property. Rather than monetary gain, the hackers were looking for information, from patents to state secrets. This is part of the reason that researchers believe the hackers to be state-sponsored actors.
Due to the sensitive nature of these targets’ information, most victims did not reveal exactly what the hackers took. We do know that the hacker’s goal was intellectual property. The hackers likely stole designs and blueprints from companies, especially from defense contractors.
Hackers also targetted governments and federal agencies, with over 20 targets in that category alone. The UK’s NHS almost certainly lost confidential medical information for its patients. Hackers also stole private information and emails from the US government, not to mention legal contracts and other sensitive documents.
Who Were The Hackers?
The scariest part about Operation Shady RAT is that we still do not know who the hackers were/are. Security researchers can hypothesize that the hackers were most-likely state-sponsored. Many cybersecurity experts think that China is the nation responsible for the hack, but we still have no solid confirmation one way or the other.
The attackers’ clear goal is the main reason that researchers believe a state was sponsoring the hack. Most hackers attack people to gain money, either directly through stealing or by mining data and selling that data to interested parties. The Shady RAT hackers were stealing information that has no commercial value on its own.
Although the data has no direct commercial value, the economic value to a nation could be staggering. With inside information on the development going on in other countries’ biggest companies, it’s possible to produce cheap, competing products, or even get ahead of the competition entirely.
How Did They Pull off This Hack?
The general public often doesn’t give social engineering the weight that it deserves. When it comes to hacking, the most common kind of hack utilizes social engineering. This method is so popular because, while companies and governments will upgrade security, they often fail to enact new protocols to make their systems safer. Human-beings are the weak link in terms of high-level cybersecurity.
The hackers behind Shady RAT first identified key people who worked at the companies and entities they targeted. These key people then received emails designed to make them want to open the attached file. In many cases, hackers lace these simple files with trojan horses. Trojan Horses are a type of malware that pretends to be safe, trustworthy software. Once installed, this malware established a connection to a remote server the hackers operate.
With a connection secretly established, the hackers helped themselves to mountains of private data before the security hole was discovered. In some cases, the victims closed these remote connections within a month. In the worst-case scenario, a connection to a remote server was maintained on-and-off for 28 months.
The Lessons of Operation Shady RAT
Shady RAT isn’t just a scary story; it’s an important lesson about the wide-reaching ability of state-sponsored hackers.
The hackers behind Shady RAT have been attacking foreign entities since 2006, but they’ve likely been operating for much longer. They managed to hack an incredible number of targets over 5 years, and it took a large-scale research team to uncover it.
These days, people rarely talk about Operation Shady RAT, but many experts conclude that it is still ongoing.
The most important takeaway from Shady RAT is that it doesn’t matter what level your company or organization is. If you own or control sensitive data, then your company can easily become a target for hackers. Even non-state hackers have a chance of breaching a system no matter what your cybersecurity measures are.
It’s now, more than ever, important for everyday people to be aware of cybersecurity risks and social engineering. If you run a company, ensure you educate your employees on the signs of social engineering. You can be paying out millions of dollars for your security, but it’s meaningless if your staff are not security savvy.
Hackers targeting you or your company? Get immediate help here.
Worried about your security? Our comprehensive security audit can help you.
Featured image by Pressmaster from Shutterstock.com